Which of the Following Best Describes Public Key Encryption
Anyone can encrypt with the public key and anyone can decrypt with the private key B. ____________ encryption is a method of encryption involving one key for both encryption and decryption Symmetric Historically it has been observed that computer processing speeds tend to double every two years.
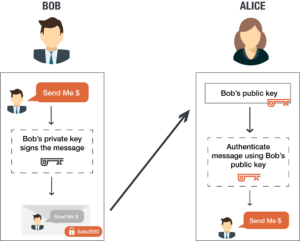
Public And Private Encryption Keys Preveil
C A user can decide to share his public key with anyone the user wishes to share withAll receiving users can make use of the public key and a.

. 2 Answers John Adney Answered Oct 19 2017 Public key can only encrypt and private key can only decrypt. The other key is known as the private key. The following statement best describes encryption on 9 The following statement best describes encryption on the internet.
Key escrow Correct Answer. A certification authority is an entity that issues digital certificates for use by other parties. Public Key Encryption.
D Publicly known and thoroughly tested encryption and decryption algorithms. A Securing stored data B Securing transmitted data C Verifying data D Authenticating data. Used prevalently on the web it allows for secure messages to be sent between parties without having to agree on or share a secret key.
This is known as Public Key Encryption. Public key cryptography is used to create publicprivate key pairs and public key. A A symmetric algorithm B A type of key C A way of encrypting data in a reversible method D A key escrow system Show Answer The Correct Answer is- C 12.
A Public Key database ensures 3rd party accountability of security. In symmetric key encryption the same key is used for encryption and decryption where as asymmetric key uses private key for encryption and decryption In symmetric key encryption the public key is used for encryption. The process of changing the ciphertext to the plaintext that process is known as decryption.
Use your own words. The second key called the private key is kept secret so that only you know it. It uses an asymmetric encryption scheme in which the encryption key is made public but the decryption key is kept private.
A It has a key size of 168 bits and its effective key size is 112. CBC-MAC uses the first block for the checksumC. A certification authority is a type of encryption that uses a public key and a private key pair for data encryption.
B A large enough keyspace to prevent attackers from easily guessing the key. One answer is the usage of asymmetric encryption in which there are two related keys usually called a key pair. Which of the following best describes PGP.
Which of the following correctly describes the difference between public key cryptography and public key infrastructure. HMAC uses a symmetric key and a hashing algorithm. Anyone who knows the secret key can decrypt the message.
To decrypt the senders message only the recipients private key may be used. QUESTION 73 Which of the following describes a component of Public Key Infrastructure PKI where a copy of a private key is stored to provide third-party access and to facilitate recovery operations. Public key encryption is an encryption method which relies on separate keys for encrypting and decrypting information Fill in the blank.
Public key encryption is an encryption method which relies on separate keys for encrypting and decrypting information. CBC-MAC is used to encrypt blocks of data for confidentialityB. Which of the following best describes the difference between HMAC and CBC-MACA.
The two types of PKC algorithms are. Public key encryption or public key cryptography is a method of encrypting data with two different keys and making one of the keys the public key available for anyone to use. A message sender uses a recipients public key to encrypt a message.
Public key can encrypt as well as decrypt private key can only decrypt John Smith Answered Dec 09 2016 You do not need an existing security setup Public key can only encrypt and private key can only decrypt. SSL is a mechanism for which of the following. Choose the answer that is NOT a feature of Public Key Cryptography.
AA cryptographic security mechanism that uses two separate sets of public and private keys to encrypt and decrypt data bA cryptographic security mechanism that uses public and private keys to encrypt and decrypt data cA cryptographic security mechanism that uses the same key for both encryption and decryption. A certification authority is a technique to authenticate digital documents by using computer cryptography. B Encryption assists in an overall security program.
A A secure channel to get the key to both participants of a communication. Which of the following is true about Public Key Encryption. Public key cryptography is the use of an asymmetric algorithm while public key infrastructure is the use of a symmetric algorithm.
HMAC creates a message digest and is used for integrity. Which of the following best describes Triple DES. A 2N Keys b N Keys c N keys d None of the above 15.
Anyone can encrypt with the public key only one person can decrypt with the private key C. Anyone can encrypt with the private key only one person can decrypt with the public key D. Public key cryptography PKC is an encryption technique that uses a paired public and private key or asymmetric key algorithm for secure data communication.
Asymmetric is a form of Cryptosystem in which encryption and decryption are performed using different keys-Public key known to everyone and Private key Secret key. Public key encryption is when an encryption is done with two keysOne of the keys is referred to as the public key while the other is referred to as a private key. The public key is made freely available to anyone who might want to send you a message.
Which of the following statement correctly describes the difference between symmetric key encryption and asymmetric key encryption. Which of the following statement correctly describes the difference between symmetric key encryption and asymmetric key encryption. There are three main types of cryptographic algorithms.
1 secret key 2 public key and 3 hash functionsPick an algorithm for any one of these types eg DES AES RSA MD5 and describe how it works and where it is applied For example SSL uses 3DES or DES for message encryption. A Encryption completely protects your data. C Encryption only works.
The true statements about the public key are b and c because. In symmetric key encryption the same key is used for encryption and decryption where as asymmetric key uses private key for encryption and decryption In symmetric key encryption the public key is used for encryption. HMAC provides integrity and data origin authentication.
C An algorithm that is only known to the participants of the communication. B It has a key size of 112 bits and its effective key size is 112. In Asymmetric key cryptography what is the required number of public keys for Nusers.

Public Key Encryption Article Khan Academy
Public Key Encryption Article Khan Academy
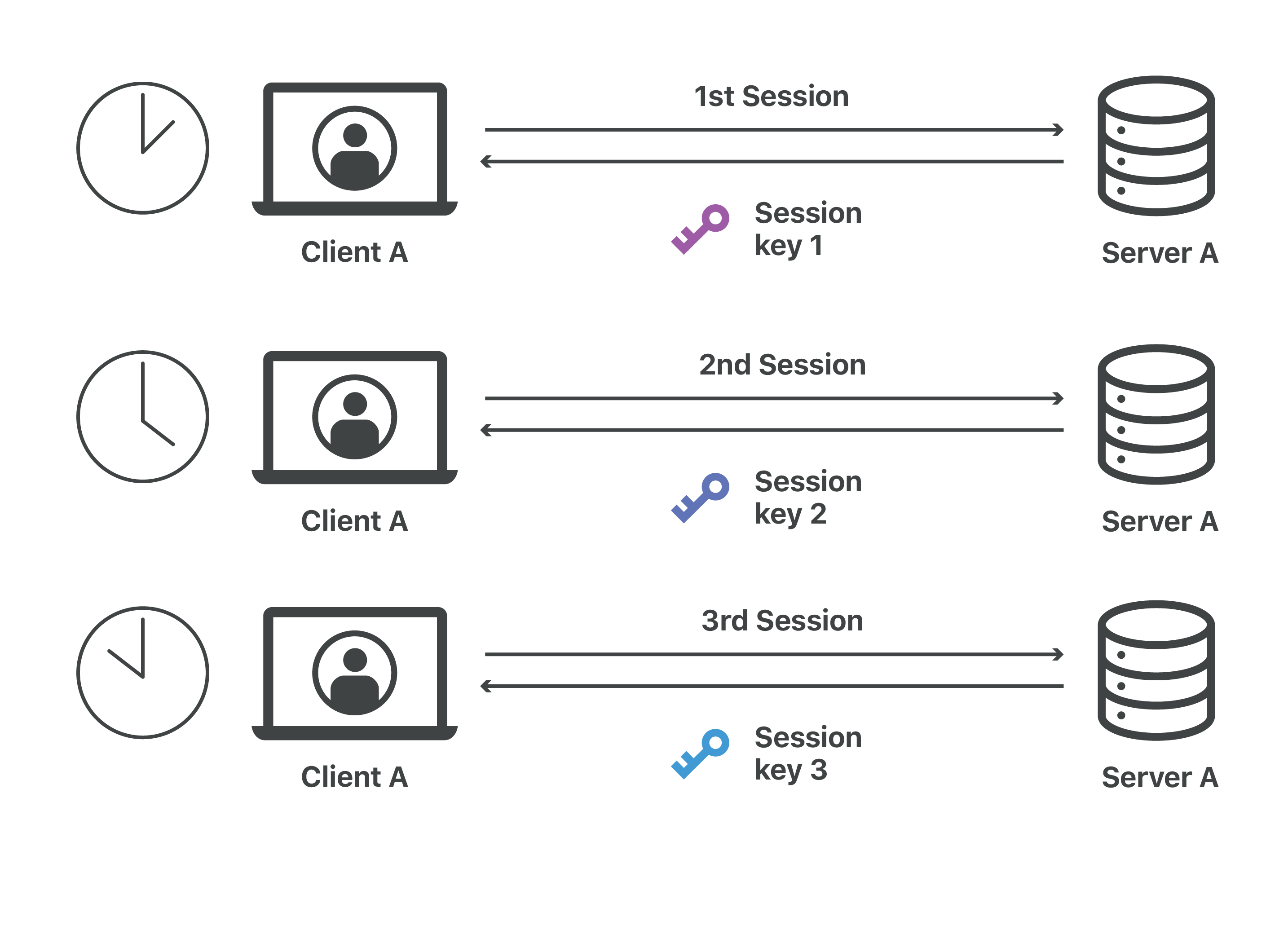
What Is A Session Key Session Keys And Tls Handshakes Cloudflare

Public And Private Encryption Keys Preveil
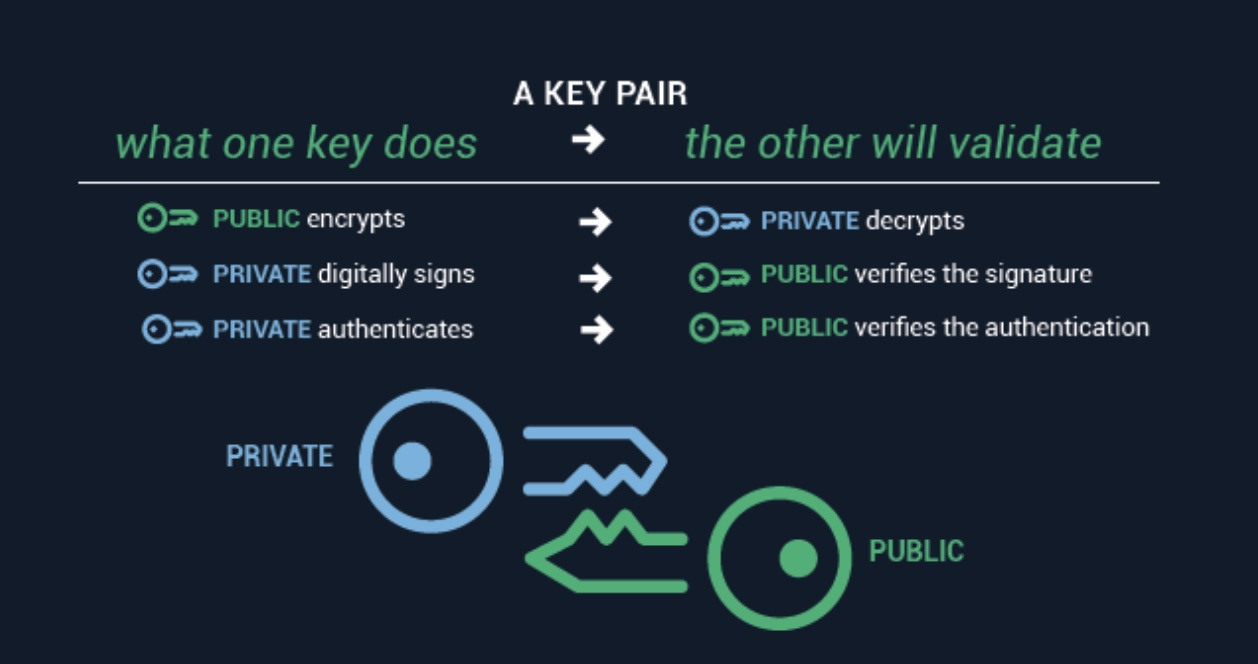
Public Key Cryptography Explained Sectigo Official

Public Key Cryptography Explained Sectigo Official
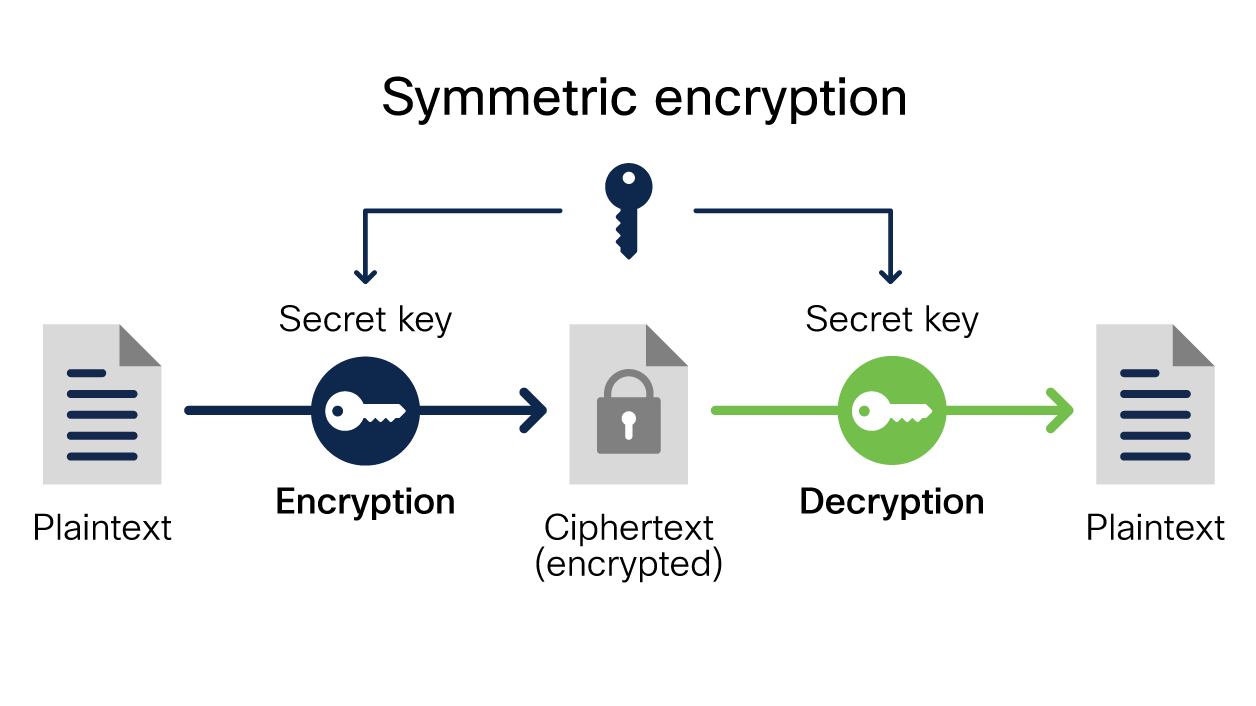
What Is Encryption Explanation And Types Cisco

Pki Explained Public Key Infrastructure

Public Key Encryption An Overview Sciencedirect Topics

What Types Of Encryption Are There Ico

Pki Explained Public Key Infrastructure

Public Key Encryption An Overview Sciencedirect Topics

Si110 Asymmetric Public Key Cryptography

Public Key Encryption Decryption Download Scientific Diagram

Public Key Encryption Article Khan Academy

Public Key Encryption Decryption Download Scientific Diagram

All About Ssl Cryptography Digicert Com

Illustration Of The Diffie Hellman Key Exchange Encryption Algorithms Cryptography Algorithm

Comments
Post a Comment